Red Team Infrastructure - Deploying Havoc C2 via Terraform
Learn how to deploy Havoc C2 (team server and client) in AWS via Terraform.
In previous posts, we laid out the foundational red team infrastructure in AWS using Terraform. The configuration included the creation of a Virtual Private Cloud (VPC), public and private subnets, route tables, an internet gateway, a Kali Linux EC2 instance with SSH access and a Windows Server EC2 instance with RDP access.
In this post, this infrastructure takes a significant step forward with the deployment of a dedicated command and control (C2) server. The goal is to deploy Havoc C2 team server on an Ubuntu 24.04 EC2 instance and configure the existing Kali machine to run the Havoc client—completing the end-to-end command and control setup often required in red team operations.
Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.
Why Havoc C2?
When planning infrastructure for red team engagements, selecting the right C2 framework is essential. Commercial C2 platforms such as Cobalt Strike or Brute Ratel are feature-rich but expensive. Many open-source alternatives like Sliver or Covenant offer potential, but they are primarily command-line driven and lack intuitive UIs, which can be a barrier for operators used to graphical workflows. Havoc C2 fills this gap. It is open-source, feature-rich, and includes a graphical interface that provides an accessible and professional feel.
EC2 instance and other configuration
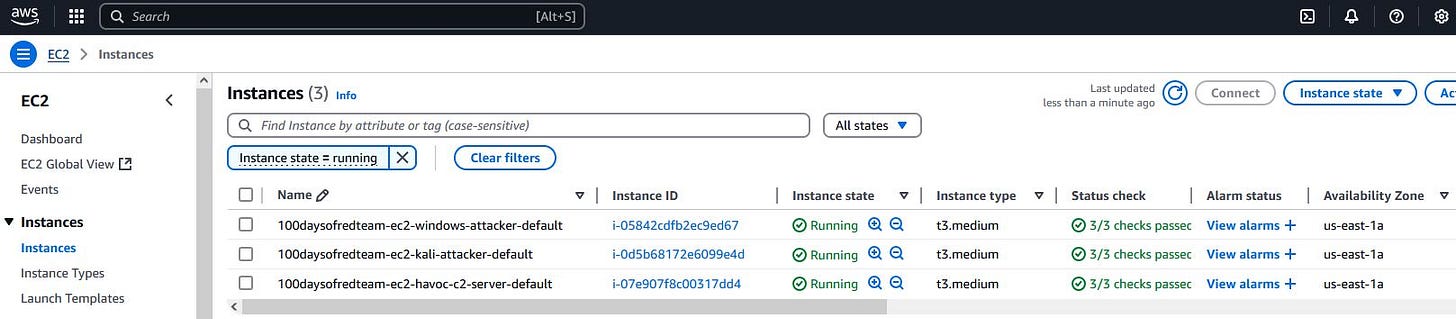
To deploy the Havoc team server, a new t3.medium Ubuntu 24.04 EC2 instance is added to our red team infrastructure. This instance will be attached to the existing public subnet. Users will be allowed to connect to the instance via SSH (key-based authentication). SSH access will be allowed over the internet (for now) but will be restricted to the user’s public IP address.
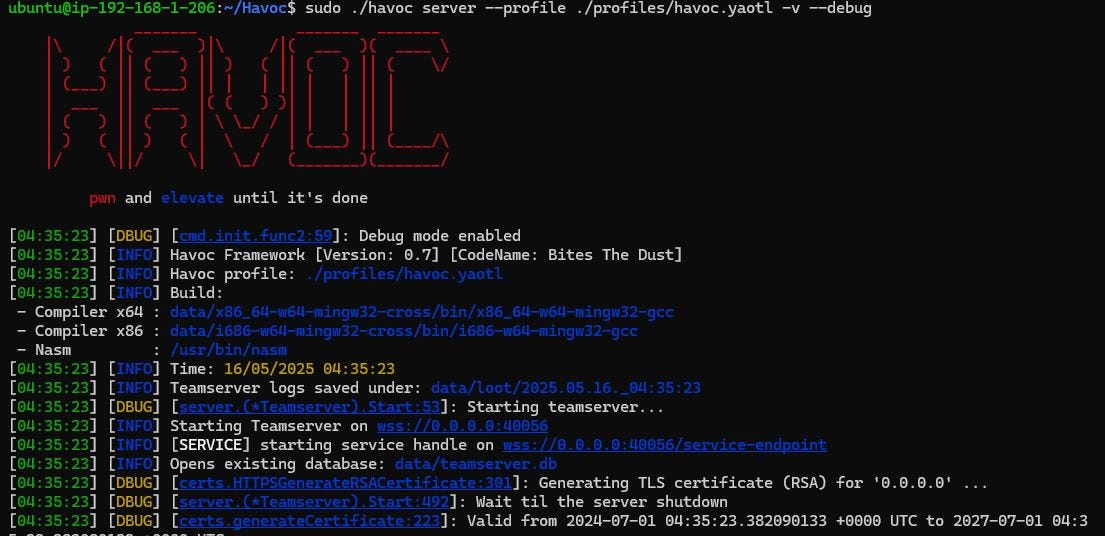
Havoc C2 installation is automated by passing an initialization bash script as a template file to the EC2 instance via user_data argument. This bash script will install all necessary dependencies, clone the Havoc GitHub repository and compile the Havoc server.
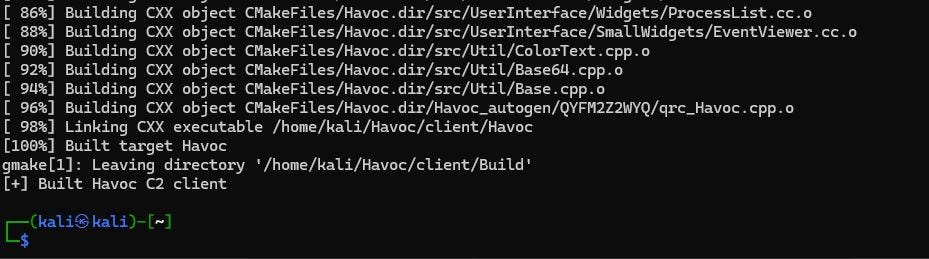
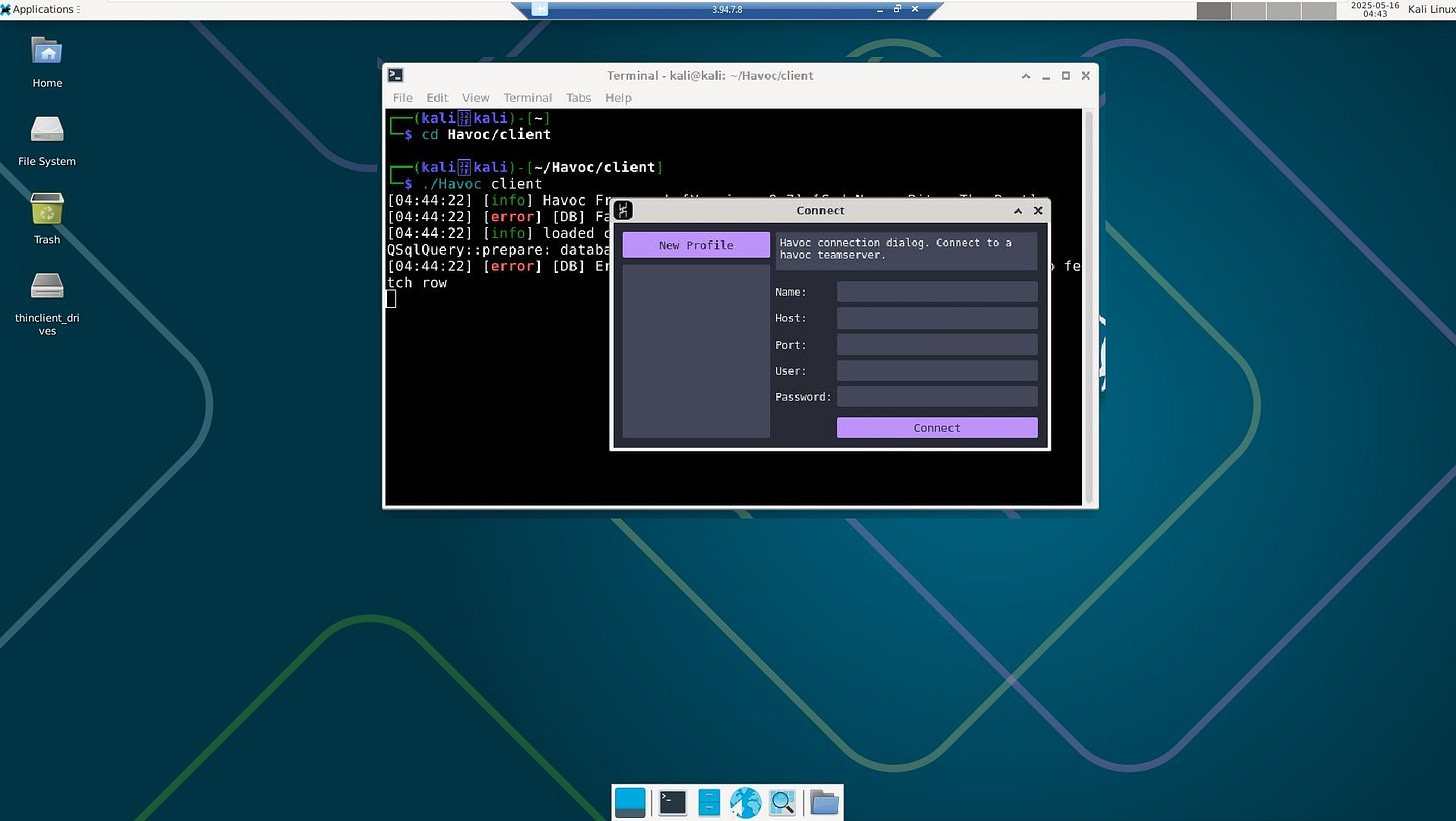
Havoc C2 provides a GUI-based client interface. To be able to access it a machine with Desktop interface is required. This can be approached in a couple of ways. The first approach is to leverage the WSL on the Windows machine. The second approach is to enable RDP access on the Kali Linux machine and deploy the client on it. We will be going with the second approach, primarily to reduce the setup time.
To enable RDP access and deploy Havoc C2 client on the Kali machine, I have updated it’s initialization bash script to include relevant commands. I also changed the instance type of the Kali Linux EC2 from t3.small to t3.medium. This change was required for successful compilation of Havoc C2 client.
Finally, the ingress rules in the security group are updated to allow access to port 40056 from within the public subnet. Port 40056 is the default port for Havoc C2 team server.
Deploying Havoc C2
Refer to the Kickstarting red team infrastructure automation via Terraform to understand the architecture we are working with.
Here is the Terraform Red Team Infrastructure project in 100 Days of Red Team GitHub repository that deploys Havoc C2.
Clone this project to your machine and execute the following commands to deploy the infrastructure:
⚠️Reminder: Switch to the dev Terraform workspace (terraform workspace select dev) before executing following commands. To create dev workspace use, terraform workspace new dev.
terraform init
terraform plan -var-file "secrets.tfvars"
terraform apply -var-file "secrets.tfvars"Reminder: You must create a
secrets.tfvarsfile manually to hold credentials. Never commit secrets to version control. It contains AWS credentials temporarily stored in plain text, which is not recommended for production environments. Also, we are still using local state files for simplicity. In a real red team deployment, you must use an encrypted remote backend.
Once done, remember to destroy the infrastructure via following command (or you may incur significant costs):
terraform destroy -var-file "secrets.tfvars"TL;DR
In this post we covered how to:
- Deploy an Ubuntu 24.04 EC2 instance using the official Ubuntu Server AMI.
- Deploy and build Havoc C2 team server on the Ubuntu EC2 instance.
- Deploy and build Havoc C2 client on the Kali Linux EC2 instance.
- Enable RDP access to the Kali Linux EC2 instance.
- Executing Havoc C2 client via RDP access to the the Kali Linux EC2 instance.Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.