Red team infrastructure - VPC creation with Terraform
Learn how to plan CIDR blocks for scalable infrastructure and deploy a VPC in AWS via Terraform
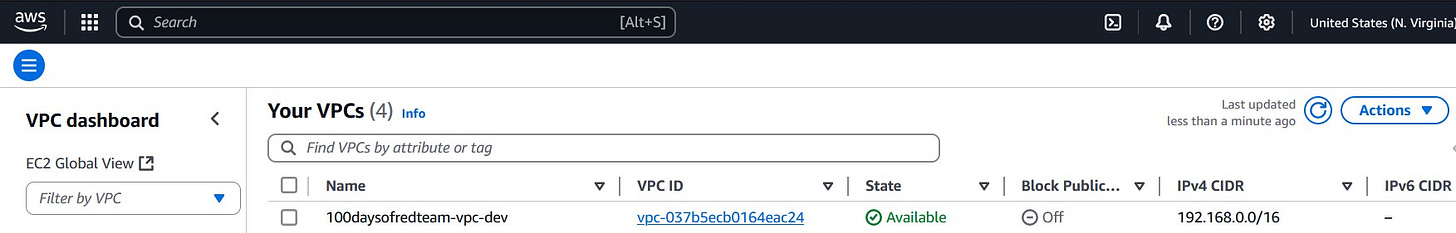
Before any cloud-based red team infrastructure can be deployed, the first foundational element that must be created is a Virtual Private Cloud (VPC). A VPC is like a virtual data center inside a public cloud provider. It allows teams to carve out a logically isolated section of the AWS cloud where they can launch resources within a defined boundary. In this post, I deploy a VPC using Terraform that will serve as the base for the remaining infrastructure.
Terraform resources for aws_vpc
Terraform provides the aws_vpc resource to define a new VPC. At a minimum, it requires a CIDR block, which is the range of IPs available within that VPC. You can also define optional settings such as DNS support and custom tags.
Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.
Here’s the syntax for provisioning aws_vpc resource:
resource "aws_vpc" "main" {
cidr_block = var.vpc_cidr
enable_dns_support = true
enable_dns_hostnames = true
tags = {
Name = "100daysofredteam-vpc-${var.environment}"
Project = "Red Team Infrastructure"
}
}We will define this resource inside a module, so that the same code can be used across different environments or targets. Tags are important here—they help with resource tracking, cost visibility, and cleanup automation. We will tag all resources with the format:100daysofredteam-<resource_type>-<workspace-name>.
CIDR block planning
Before defining the VPC in Terraform, it’s crucial to plan the CIDR block. A CIDR (Classless Inter-Domain Routing) block defines the IP range for your VPC. For example, 192.168.0.0/16 offers up to 65,536 IP addresses, which is sufficient for most red team infrastructures. Smaller VPCs (e.g., 192.168.0.0/24) might make sense for tightly scoped engagements or limited infrastructure.
A simple planning table might look like this:
VPC CIDR Block = 192.168.0.0/16
Public Subnet A = 192.168.1.0/24
Private Subnet A = 192.168.2.0/24This block-level planning enables red team operators to anticipate subnet placement, NAT gateway routing, or VPN configurations later.
Deploying the VPC
Let’s walk through the directory structure and the Terraform code needed to define and deploy the VPC using a modular approach.
Refer to the Kickstarting red team infrastructure automation via Terraform to understand the architecture we are working with.
We will use the following directory structure:
vpc/
├── main.tf
├── variables.tf
├── outputs.tf
├── secrets.tfvars # <--- manually created, not committed
├── terraform.tfvars
├── modules/
│ └── vpc/
│ ├── main.tf
│ ├── variables.tf
│ └── outputs.tf
├── providers.tfFor red team automation, a custom VPC is the starting point for building isolated, disposable infrastructure that avoids noisy defaults and supports stealth tactics like subnet segmentation or NAT evasion.
Note: Currently, we are using local state files, stored on disk in
terraform.tfstate. These files contain metadata about all deployed resources, and often include secrets or sensitive values. Unencrypted local state files are not secure and are suitable only for learning or development purposes. Later in the series, we will migrate to remote encrypted state backends using S3 and DynamoDB for locking, versioning, and collaboration.
Here is the Terraform Red Team Infrastructure project in 100 Days of Red Team GitHub repository that deploys a VPC in AWS.
Note: The
secrets.tfvarsfile must be created manually and should never be checked into version control. It contains AWS credentials temporarily stored in plain text, which is not recommended for production environments.
Clone this project to your machine and execute the following commands to deploy a VPC:
Following permissions need to be added to the
TerraformEC2AccessIAM policy before using the above mentioned project:
ec2:CreateVpc
ec2:ModifyVpcAttribute
ec2:DeleteVpc
terraform workspace new devterraform init
terraform plan -var-file "secrets.tfvars"
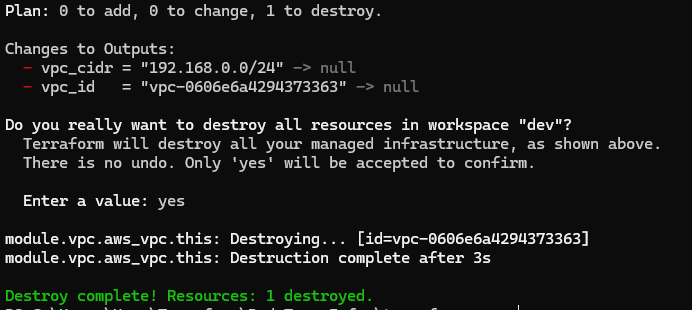
terraform apply -var-file "secrets.tfvars"Once done, remember to destroy the VPC via following command:
terraform destroy -var-file "secrets.tfvars"TL;DR
- Deploy a custom AWS VPC using Terraform using a modular approach.
- Planning CIDR blocks is essential to build scalable infrastructure.Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.