What is Early Bird code injection and how it enables red team trade-craft?
Learn what is Early Bird code injection technique and how to use it for red team trade-craft.
If a red team operator can slip-in their code even before the anti-malware solution gets to it, wouldn’t that be sweet!
That’s what the Early Bird code injection technique achieves.
Before diving into this technique, lets understand what are Asynchronous Procedure Calls (APC). In simple terms, APC tells a thread which task it is supposed to work on next as and when it takes a break i.e. enters an alertable state. An alertable state of a thread refers to a condition where the thread is actively waiting and is prepared to respond to asynchronous events. A thread enters an alertable state when it calls either of the following Windows APIs:
If the APC is queued on a thread and it does not enter alertable state, the APC remains queued until the thread calls another alertable wait function.
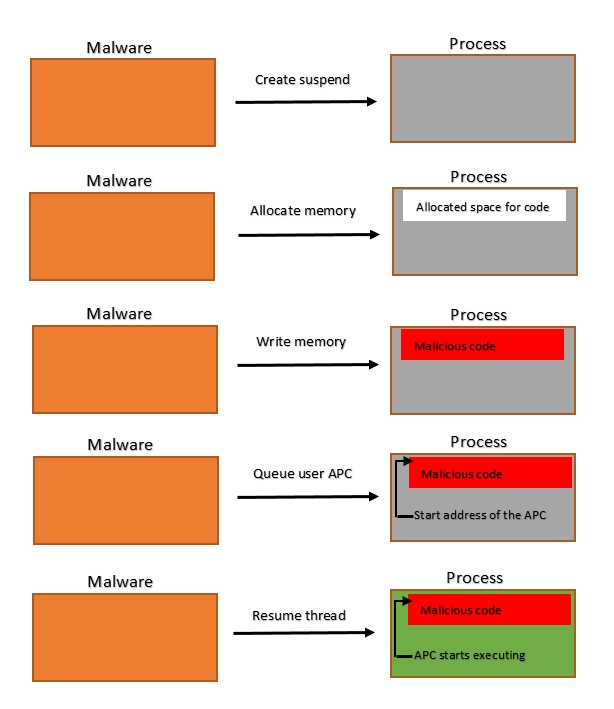
Now, a red team operator can take advantage of this by queuing the APC to a process’s main thread so early in the process creation stage that it bypasses the anti-malware hooks. The flow for this is as follows:
A red team operator controlled program creates a new process in the suspended state.
It then allocates the memory for shellcode in the newly created process's address space.
Creates an APC that points to the shellcode memory location.
Writes the shellcode to the allocated memory.
Queues the APC to the main thread (which is in suspended state).
Finally, resumes the thread which in turn executes the shellcode.
If this sounds a lot like fork & run that’s because it is a variation of fork & run technique. The advantage this technique has over other fork & run techniques is that in this technique the malicious code is executed early in the process creation phase, hence the name Early Bird. This enables it to evade scanning and makes it stealthier in comparison.
Red Team Notes
- Early Bird code injection is a fork & run process injection technique which leverages Asynchronous Procedure Call (APC) to execute malicious code early in the process creation phase.
- It is stealthier than other fork & run techniques as code execution happens before anti-malware scanning. Caveats related to fork & run still apply though. Follow my journey of 100 Days of Red Team on WhatsApp or Discord.
If you want to deep dive into the technical details of this technique, refer to New ‘Early Bird’ Code Injection Technique Discovered by Hod Gavriel and Boris Erbesfeld and Early Bird APC Queue Code Injection by Mantvydas Baranauskas. The post by Mantvydas contains the proof-of-concept code as well.