WebSockets handshake for red team professionals
A simple guide to understanding the WebSockets handshake and how red teams can leverage it.
A WebSocket is a full-duplex, persistent connection between a client (usually a browser) and a server, used to exchange messages with low latency. Unlike HTTP’s request/response model, a WebSocket connection allows both endpoints to send data anytime after the connection is established. The connection is negotiated starting from a normal HTTP (or HTTPS) request called the handshake. Understanding the handshake is critical because it’s where the protocol transitions and where adversaries can intercept, manipulate, or abuse connections.
The WebSocket handshake
The handshake is an HTTP Upgrade dance that upgrades an HTTP(S) connection to the WebSocket protocol (RFC 6455). Key steps performed during the handshake are as follows:
Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.
Client initiates with an HTTP GET request
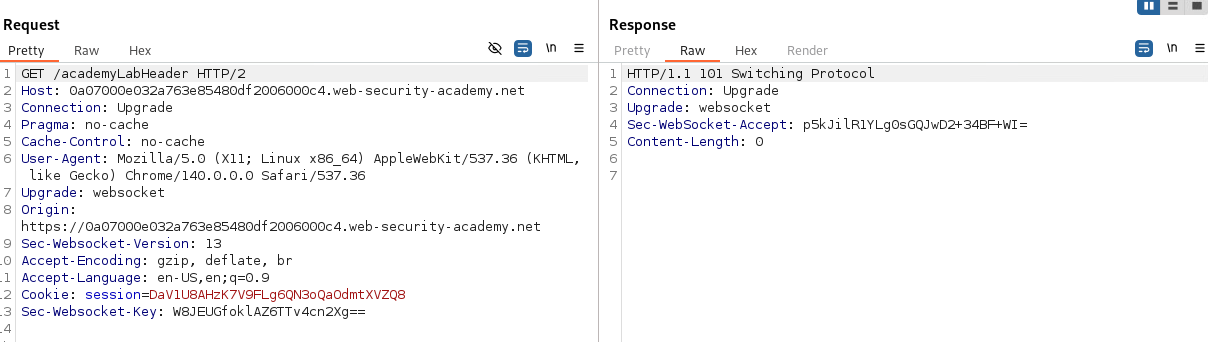
The client sends a GET request to the server containing following special headers:
Upgrade: websocketConnection: UpgradeSec-WebSocket-Key: <random-base64>— a nonceSec-WebSocket-Version: 13Optional:
Sec-WebSocket-Protocol: <subprotocol>andOrigin: <origin>
Server responds with HTTP 101 Switching Protocols response
If the server accepts, it responds with following headers:
HTTP/1.1 101 Switching ProtocolsUpgrade: websocketConnection: UpgradeSec-WebSocket-Accept: <base64-sha1-of-key+GUID>Optionally echoes a chosen subprotocol in
Sec-WebSocket-Protocol.
The
Sec-WebSocket-Acceptis computed as:Concatenate the client
Sec-WebSocket-Key(raw value) and the GUID258EAFA5-E914-47DA-95CA-C5AB0DC85B11.Compute SHA-1 over that string.
Base64-encode the SHA-1 digest.
Connection moves to binary framing
After the 101 response, the TCP connection switches from textual HTTP to WebSocket frames. Frames have an opcode, length, masking bits (clients must mask), and payload.
How red teams can leverage WebSocket handshakes?
For red teams, this handshake offers several advantages:
Protocol negotiation as a covert channel entry point - Subprotocols and headers can be used to smuggle metadata (e.g., agent ID) at connection time without sending an obvious payload. Because many applications accept arbitrary
Sec-WebSocket-Protocolvalues, a red-team implant can hide a token inside that header at connect time.Leveraging legitimate, long-lived channels for C2 - Compromising or abusing a legitimate WebSocket endpoint allows persistent bidirectional control with low detectability. A red team operator can embed an agent on an internal host that opens a WebSocket to a cloud service the organization already trusts.
Handshake-based reconnaissance and endpoint discovery - Sending crafted handshake requests can reveal endpoints and server behavior (subprotocols supported, origin enforcement etc.). Responses like supported subprotocols, or the absence of origin checks can leak useful information.
Bypassing HTTP filtering and proxy rules - Some proxies or filtering systems apply different rules to WebSocket traffic or allow upgrade requests to pass. A red team can piggyback on allowed
Upgradeflows or usewssto blend with HTTPS traffic.Handshake tampering & MitM for session hijack - Where TLS is not used (ws://) or TLS is weak, an attacker in the path can tamper with headers or redirect the handshake to a malicious backend.
If you want to experiment with WebSocket vulnerabilities, try out this learning path from PortSwigger Academy (its free). To learn more about WebSockets, check out the official WebSockets website.
TL;DR
- During a WebSocket handshake a browser sends an HTTP GET with Upgrade: websocket, Sec-WebSocket-Key, Sec-WebSocket-Version (±Sec-WebSocket-Protocol/Origin); a compliant server replies 101 Switching Protocols with Sec-WebSocket-Accept, then the connection switches to WebSocket frames.
- It creates a persistent, full-duplex channel (ws:// or wss://) so both sides can send messages anytime with low latency.
- Red team can leverage handshake headers and subprotocols to carry covert metadata, wss on 443 or stealthy C2, frames to tunnel arbitrary data, and crafted handshakes to fingerprint servers.Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.