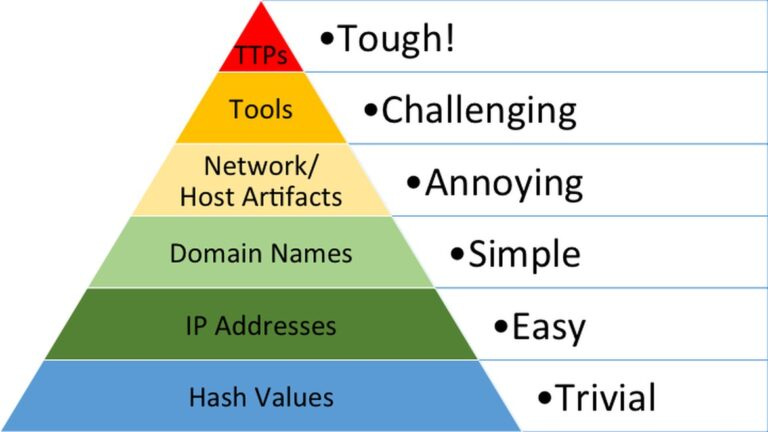
The Red Team Pyramid of Pain
A model showing how progressively advanced red team tradecraft makes it harder for defenders to detect and respond.
The Pyramid of Pain is a cybersecurity concept originally introduced by David J Bianco to illustrate the difficulty adversaries face when defenders detect and block different indicators of compromise (IOCs). The further up the pyramid defenders operate, the more challenging it becomes for attackers to adapt. While this concept is widely used in defensive security, it can also be adapted for red teaming—but with an inverted perspective.
The Red Team Pyramid of Pain represents the increasing levels of pain red teams can inflict upon blue teams by advancing their tradecraft. At the lower levels, blue teams can detect and respond to red team activity with relative ease, but as red teams refine their techniques and methodologies, defenders face greater challenges in detection and response. The higher up the pyramid, the more pain defenders experience, requiring them to invest more time, resources, and advanced detection capabilities.
Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.
Each level of the pyramid represents a different category of adversary tradecraft. At the base, simple and well-known techniques are easy for defenders to detect. As we move up, techniques become stealthier, more sophisticated, and harder to identify, demanding increasingly advanced detection capabilities.
Common TTPs (Minimal Pain) - At the base of the pyramid are well-documented, widely known TTPs. These include straightforward credential dumping with Mimikatz, pass-the-hash attacks, basic phishing campaigns, and simple malware executions. Most modern security tools can flag and block these activities based on signatures and predefined rules.
Obfuscated Techniques (Increasing Pain) - To evade basic detections, red team operators modify their techniques by using obfuscation, encoding, or encryption. This level includes base64-encoded PowerShell scripts, obfuscated command execution, custom packers for malware, and slightly altered versions of known attack tools to bypass signature-based detection. Advanced security solutions with features like anomaly detection, behavior-based analytics and heuristic scanning can help defenders mitigate these attacks more effectively.
Living-Off-the-Land (Significant Pain) - At this stage, attackers begin to blend into legitimate system activity by using tools natively available on a system. These techniques involve abusing built-in system tools such as
rundll32.exe,mshta.exe,certutil.exe, and WMI to execute malicious payloads. Since these tools are commonly used for administrative tasks, distinguishing malicious usage from legitimate activity becomes difficult. Defenders must rely on deep visibility into process behavior, event correlation, proactive threat hunting and baseline deviations to detect these attacks.Custom Malware and C2 Frameworks (Severe Pain) - To further evade detection, red team operators may employ custom malware and covert command-and-control (C2) frameworks that bypass traditional defenses. These may include fully custom implants, in-memory execution, self-deleting payloads, and encrypted C2 communications that evade network-based monitoring. Defenders must rely on behavioral forensics, memory analysis, and real-time endpoint monitoring to detect anomalies at this level.
Novel Attacks (Maximum Pain) - At this tier, red teams leverage cutting-edge attack techniques, including zero-day exploits, unconventional lateral movement strategies, and advanced exfiltration methods. Since there are no predefined signatures or established detections for these methods, defenders must rely on threat intelligence, behavioral baselining, and real-time attack simulations to detect them. Security teams operating at this level must continuously adapt and research emerging attack vectors to stay ahead of adversaries.
Adaptive Tradecraft (Unbearable Pain) - At the highest level of the pyramid, red team operators continuously evolve their tactics in real-time. This includes AI-driven attack automation, polymorphic malware that changes its code structure dynamically, and hybrid attack models combining multiple tradecraft elements. Red teams at this stage can actively respond to blue team detections and modify their techniques on the fly to remain undetected. Only the most advanced security teams, operating at the intersection of human expertise and AI-driven defense, can effectively combat adversaries at this level.
The Red Team Pyramid of Pain provides a structured way to assess both red and blue team maturity. Red teams use this model to maximize the challenge for defenders, ensuring that engagements push blue teams to improve their detection and response capabilities. For defenders, understanding where they stand on this pyramid helps in identifying gaps in detection coverage and security readiness.
Red Team Notes
The Red Team Pyramid of Pain represents the increasing difficulty defenders face as red teams advance their tradecraft, from using common techniques to adaptive attacks:
- Common TTPs (Minimal Pain) – Basic, well-known techniques like Mimikatz and simple phishing, easily detected by signature-based security tools.
- Obfuscated Techniques (Increasing Pain) – Slightly altered attack methods, using encoding, encryption, and obfuscation to bypass traditional detections.
- Living-Off-the-Land (Significant Pain) – Abuse of legitimate system tools to evade detection and blend into normal activity.
- Custom Malware and C2 Framework (Severe Pain) – Fully custom implants, in-memory execution, and encrypted C2 channels that evade traditional defenses.
- Novel Attacks (Maximum Pain) – Zero-day exploits, unconventional lateral movement, and stealthy data exfiltration techniques.
- Adaptive Tradecraft (Unbearable Pain) – Real-time tradecraft evolution, AI-driven automation, and polymorphic malware that forces defenders into a reactive posture.Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.