Quick introduction to AMSI for red team professionals
Learn what is Anti-Malware Scan Interface (AMSI) and how it works.
Imagine you are at the security check at an airport. What happens there?
You put your bags and other belongings in a couple of trays and then send them for scanning. Your trays then go through an x-ray scanner. At the other end of the scanner, there are a couple of security officers who look at the scanned contents of your trays in a screen and then decide whether they are safe or not.
In a similar way, as a developer, you can identify whether the user input in your application contains any malicious content or not, by sending it through a security check.
In Windows 10, this security check is enabled via the Anti-Malware Scan Interface (AMSI). It works in a similar way as the security check at the airport. The application sends the user input string or buffer to be scanned to AMSI via AMSI APIs (i.e. trays). AMSI then forwards this content to the anti-malware scanning engine on the machine (i.e. the x-ray scanner). The anti-malware engine scans the content and returns the result to AMSI. Finally, AMSI (i.e. security officers) evaluates the result and informs the application whether the content is safe to use or not.
In simple terms, through AMSI, Windows 10, provides a bridge to applications to interact with the anti-malware software installed on the machine for leveraging it’s security services. The anti-malware software installed on the machine must also be enabled to interface with AMSI for this to work. Microsoft Defender, Sentinel One, CrowdStrike Falcon are few such anti-malware solutions.
AMSI is integrated into these components of Windows 10:
User Account Control, or UAC (elevation of EXE, COM, MSI, or ActiveX installation)
PowerShell (scripts, interactive use, and dynamic code evaluation)
Windows Script Host (wscript.exe and cscript.exe)
JavaScript and VBScript
Office VBA macros
Excel 4.0 Macros
Volume Shadow Copy operations
.NET in-memory assembly loads
Additionally, it can also be leveraged by developers who:
Want to make requests to anti-malware products from within their apps.
Want their anti-malware product to offer their services to applications.
Below is the illustration of AMSI architecture
AMSI provides following functions for applications to interface with it:
AmsiCloseSession - Close a session that was opened by AmsiOpenSession.
AmsiInitialize - Initialize the AMSI API.
AmsiNotifyOperation - Sends to the anti-malware provider a notification of an arbitrary operation.
AmsiOpenSession - Opens a session within which multiple scan requests can be correlated.
AmsiResultIsMalware - Determines if the result of a scan indicates that the content should be blocked.
AmsiScanBuffer - Scans a buffer-full of content for malware.
AmsiScanString - Scans a string for malware.
AmsiUninitialize - Remove the instance of the AMSI API that was originally opened by AmsiInitialize.
Red Team Notes
- The Windows Anti-malware Scan Interface (AMSI) is an interface that allows applications and services to integrate with anti-malware product that's present on a machine.
- AMSI is agnostic of anti-malware vendor; it's designed to allow for the most common malware scanning and protection techniques that can be integrated into applications.Follow my journey of 100 Days of Red Team on WhatsApp or Discord.
To see AMSI in action, open a Powershell window and type ‘Invoke-Mimikatz’:
You’ll see that even though we didn’t load the actual Invoke-Mimikatz tool, the mere mention of it gets flagged.
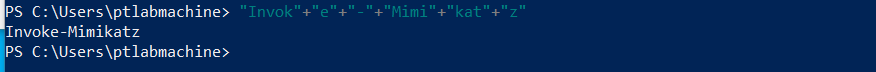
Now, type "Invok"+"e"+"-"+"Mimi"+"kat"+"z" and see if this gets flagged as well:
This time it didn’t get flagged. That’s because the underlying anti-malware engine (Defender in this case), uses signature-based detection as one of the detection mechanisms and it is relatively simple to bypass these.
To verify whether AMSI is loaded in this Powershell session, you can use a tool like Process Explorer and look at the loaded DLLs for this process: