Hunting high-value Windows Access Tokens using open-source tools
What makes a token valuable and how to use various open-source tools to hunt for high-value windows access tokens.
Imagine there’s a stack of boxes, filled with treasure, but all of them are locked. Next, you are handed over a bunch of random keys, few of which may open some of these boxes. How would you identify which keys are useful? Sure, you can try each key on every box but you are a red team operator you can do better than this.
A smarter way to do this would be to analyze locks and keys and identify attributes which may help you discard non-relevant keys. Lets say you are targeting a particular box, you can check which keys have the same brand name on them as that on the lock and eliminate the ones which have a different name. Next, you can check if the size of key is proportionate to the size of the lock and eliminate smaller or bigger keys. Next, you can check whether the key type matches the lock and eliminate the ones that are of different type.
Similarly, not all Windows Access Tokens are made alike. So how does a red team operator identify which tokens are valuable and which ones to ignore? A high-value token should have one or more of the following attributes:
High Privileges - These are tokens associated with SYSTEM, Administrator, or service accounts with privileged access.
Impersonation Capabilities - Tokens with impersonation permissions can be used to run or create processes on behalf of other accounts. These permissions are usually manifested through
SeImpersonatePrivilegeorSeAssignPrimaryTokenPrivilege.SeImpersonatePrivilegemeans that a token with this privilege can execute programs on behalf of other users.SeAssignPrimaryTokenPrivilegemeans that process can replace the access token of a child process with a different token. Processes with these privileges can be used on local machine only and cannot be used to access network resources.Delegated - These are tokens that allow access to remote systems.
Elevated - These are tokens with high integrity level. A high-integrity token means the process is running with administrative rights.
Unrestricted - Unrestricted tokens provide more freedom for executing privileged operations.
Non-sandboxed - These are tokens without sandbox attribute set (TokenSandboxInert). Only non-sandboxed tokens can be used for privilege escalation.
Next, lets have a look at desirable privileges. A high-value token should have one or more of the following privileges:
SeDebugPrivilege - Allows access to any process for memory reading/writing.
SeImpersonatePrivilege - Allows impersonation of other users.
SeAssignPrimaryTokenPrivilege - Enables creation of new processes with arbitrary tokens.
SeTcbPrivilege - Trusted Computing Base privilege, effectively granting SYSTEM-level access.
SeIncreaseQuotaPrivilege - Allows setting resource limits, useful in process injection scenarios.
SeCreateTokenPrivilege - Allows creation of new access tokens.
SeTakeOwnershipPrivilege - Grants the ability to take ownership of objects.
SeBackupPrivilege and SeRestorePrivilege - Useful for stealing sensitive files and registry hives.
SeLoadDriverPrivilege - Allows loading kernel drivers, which can lead to kernel-mode execution.
SeManageVolumePrivilege - Allows manipulation of disk volumes, useful for persistence techniques.
Finally, lets discuss some open source tools that can help in enumerating and identifying high-value tokens:
Mimikatz
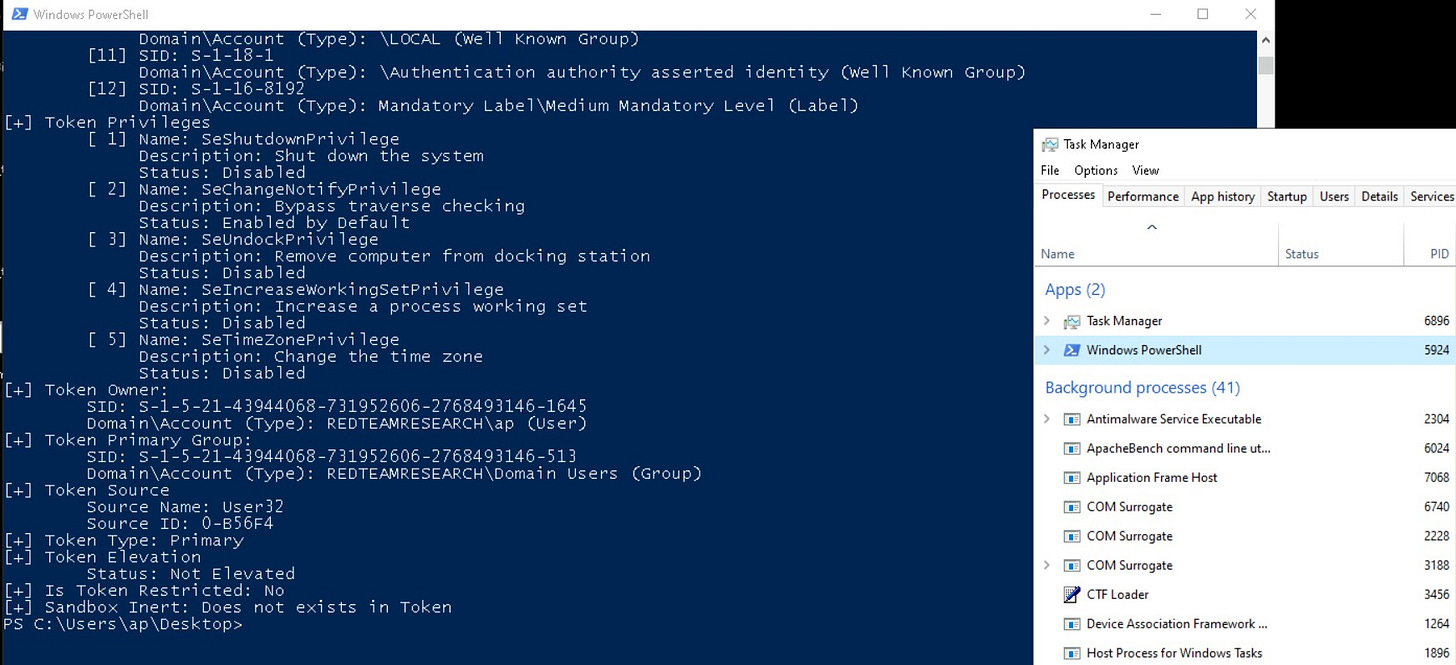
The token module of Mimikatz can be used to list tokens available on a system:
When run with administrative privileges it can list tokens from processes belonging to other users as well:
Incognito
Incognito can be used as an independent tool or as a meterpreter module for token manipulation. It also offers a feature to list available tokens on a machine:
While Mimikatz returns information about individual tokens, Incognito clubs that information to display either users or groups whose tokens are available on the machine.
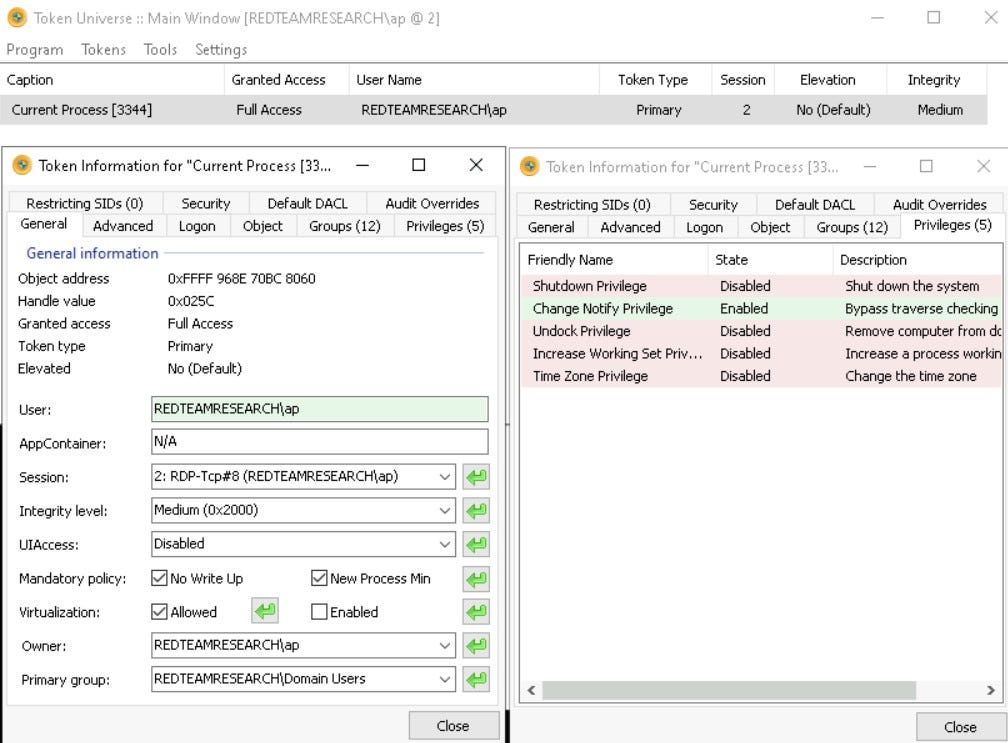
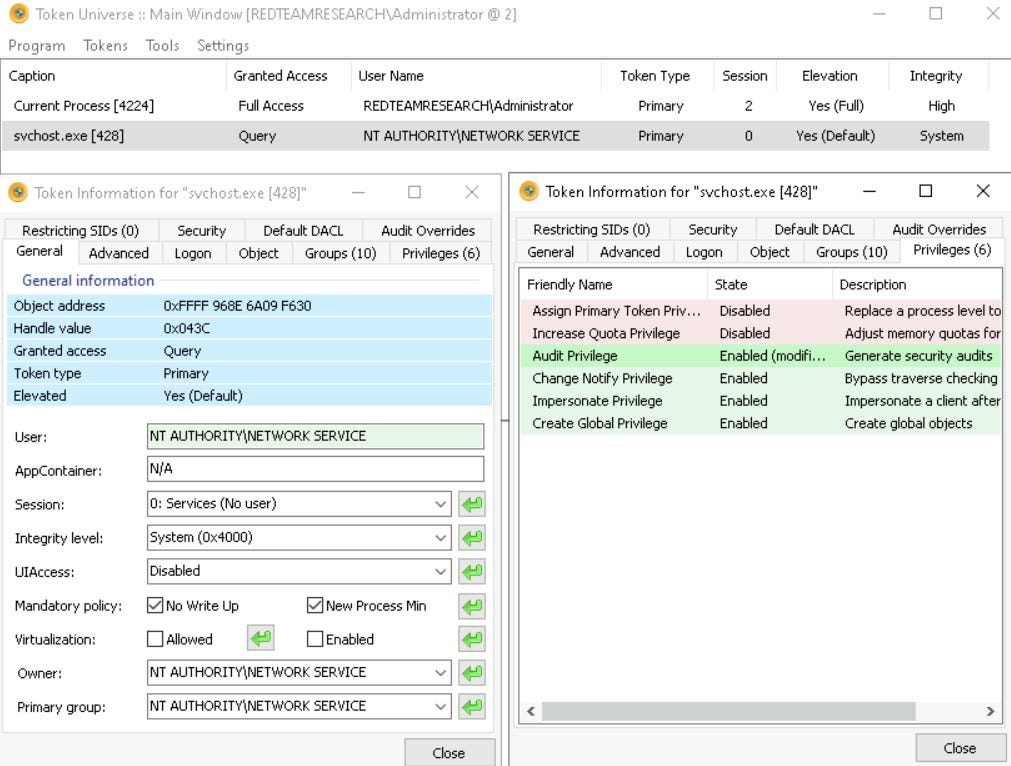
TokenUniverse
TokenUniverse is a GUI based tool specifically designed for token enumeration and manipulation operations.
Token Dump
Token Dump is a command-line tool that can be used to retrieve and display token information of a given process.
Other Tools
Other tools that can be used for Windows Access Token enumeration and manipulation:
Red Team Notes
- One or more desirable attributes of a high-value token include high-privileges, impersonation capabilities, elevated, unrestricted, non-sandoxed and delegated.
- One or more desirable privileges in a high-value token include SeDebugPrivilege, SeImpersonatePrivilege, SeAssignPrimaryTokenPrivilege, SeTcbPrivilege, SeIncreaseQuotaPrivilege, SeCreateTokenPrivilege, SeTakeOwnershipPrivilege, SeBackupPrivilege and SeRestorePrivilege, SeLoadDriverPrivilege, SeManageVolumePrivilege
- Tools that can be used for enumerating Windows Access Tokens include Mimikatz, Incognito, TokenUniverse, Token Dump, Tokenvator, TokenPlayer, Process Explorer and Process Hacker.Follow my journey of 100 Days of Red Team on WhatsApp, Telegram or Discord.